You are sometimes horrified by the thought that your child does not leave his computer all day, but at the same time you have no control over this process!
Or have you recently begun to feel that your loved one is hiding something from you? Not a single message is stored in his ICQ, all files from the computer were transferred to a USB flash drive, he works on the Internet only when you are not around!
Sales of your company fell by 50% and the best manager began to behave inappropriately sometimes? When you enter, he frantically presses something on the keyboard!
You cannot understand what is happening. We do not offer you to spy on a child, loved one or employee - we offer you a reliable assistant in obtaining the necessary information - keylogger KGB Spy. KGB Spy will unravel all the secrets!
The principle of operation of "keylogger"
"How does he work?" - you will say with surprise when you receive a letter with a detailed report on the user's work on the computer from KGB Spy to your email inbox. KGB Spy does its job even better than the famous agent 007 James Bond.
The functionality of the program allows you to set the invisible operation mode of KGB Spy, so that no one will guess that a real "keylogger" is watching him. KGB Spy discreetly monitors the operation of the computer: it records information entered from the keyboard, data from the clipboard, and monitors visited sites.
The information collected during monitoring is stored in a database to which only you have access. You can receive a letter to your email box with detailed information about who, when and what did on the computer. You just need to check your mail from time to time.

Capabilities of the KGB Spy
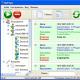
Convenient and clear interface
We have tried to make the KGB Spy interface as convenient and understandable as possible for everyone, even for novice computer users.
Interception of pressed keys on the keyboard
KGB Spy logs all the keys that the user presses on the keyboard.
Recording screenshots (screenshots)
KGB Spy records not only information entered from the keyboard and data from the clipboard, but also takes screenshots (screenshots).
Interception of ICQ, Qip, Mail.ru Agent, etc.
KGB Spy intercepts all messages in the most common instant messaging programs such as Icq, Miranda, Qip, Yahoo! Messenger, Windows Live Messenger, Skype 3, Google Talk.
Clipboard monitoring
One of the main functionality of the program is to monitor the content of information in the clipboard, which every computer user without exception works with.
Monitoring of visited websites
Keeping a firm's bank account in positive balance and moderate Internet traffic - isn't that the dream of any company executive? Make your dream come true with KGB Spy, which will give you a complete report on all websites visited by the user. By the way, this is also a solution to the problem for parents who are worried about the content of information received from the Internet by their child.
Visible/invisible operation mode
The program has two modes of operation: visible and invisible. Moreover, if you select invisible mode, then users will not notice the work of KGB Spy.
Monitoring the launch and closing of programs
Each computer, in addition to the operating system installed on it, also has in its arsenal a sufficient number of programs necessary for work. KGB Keylogger monitors the launch and closing of programs. This function can be useful both for finding out the causes of any technical problems, and for determining the timeliness or untimeliness of using a particular software application.
Monitoring computer on/off/restart
In the XXI century, the computer has become an integral part of the life and work of any person. But in every mechanism there are tools that are very difficult to control. KGB Spy monitors the on/off/restart of the computer and allows you to quickly monitor the events taking place with the machine/machines.
Full multi-user support
It doesn't matter how many users you have on your system. KGB Spy can spy on individuals, such as children, or everyone.
E-mail notifications about a set of forbidden words
If a user types a signal (forbidden), then KGB Spy will mark this entry in the log with a special label or send you a notification by e-mail.
USER AND OPERATOR OF THE INFORMATION SYSTEM
When determining the presence or absence of a sanction for actions with information in an information system, it is important to clearly understand the difference between the concepts of "user" (programs or computers) and "information system operator". The concept of "user" is commonly used in many areas of human activity (there are concepts of "property user", "wildlife user", "subsoil user", "work user", "user of communication services", "computer user", etc.) , and the concept of "information system operator" is a special legal one, defined in the law and not requiring interpretation.
Let's try to deal with the user first. Ushakov’s explanatory dictionary of the Russian language says that a user is “a person who has some kind of property in use, in operation”, that is, on the one hand, a user can be understood as a person using a computer. However, in accordance with Art. 1280 of the Civil Code, a user is “a person lawfully owning a copy of a computer program or a copy of a database”, Thus, the word “user” can also be used to define the owner of a copy of a program or database. Which of these two concepts applies to our case? Since illegal access to information and the creation of malicious programs should be considered only in the context of relations with information (and not relations with intellectual property), the conclusion is unambiguous - in our case, it is necessary to be guided by the interpretation of Ushakov's dictionary. Therefore, in the context of Chapter 28 of the Criminal Code, a user is any person who uses a computer.
Now back to the information system operator. According to the definition given in Article 2 of the Federal Law "On Information ...", "an information system operator is a citizen or legal entity engaged in the operation of an information system, including the processing of information contained in its databases." If we limit ourselves to this definition, we can draw the wrong conclusion. that “user” and “information system operator” are one and the same. However, in Part 2 of Art. 13 of the same law states: “unless otherwise provided by federal laws, the operator of the information system is the owner of the technical means used to process the information contained in the databases, who lawfully uses such databases, or the person with whom this owner has concluded an agreement on the operation of the information system ". That is, we are not talking about any user, but either about the owner of computer equipment, or about the person whom the owner hired to manage this equipment. Thus, both, for example, a family member of the owner of a home computer, and an employee of a company working on corporate equipment, being a computer user, is not an information system operator. Therefore, one cannot say that it is necessary to obtain permission from such a user to access information - he simply does not have the rights to give such a sanction. But the owner of a home computer or the director of a company that owns computer technology has such rights, which is clearly stated in the law. Accordingly, if access to information is authorized by the operator of the information system, then whether an ordinary user wants or does not want this access to be carried out, this does not bother anyone - the operator of the information system exercises his legal right.
The main conclusion from the difference described above is this. It is impossible to consider access to information without the authorization of the user, but with the authorization of the operator of the information system (which is implemented at the technical level using the administrator's password) illegal, and the program that implements such access is malicious.
If an ordinary user stores his own information in the information system of the employer (or relative or acquaintance), then he, as its owner, formally has the right to allow or deny access to it. However, as follows from the law and practice, the permission or prohibition of "technical access" to information stored in the information system is controlled by its operator, and the owner of the information does not have the right to interfere in the management of the information system.
The result is the following. If an ordinary user, as the owner of his own information, has an agreement with an information system operator and this agreement provides that the user has the right to store his own information in someone else's information system, and the information system operator undertakes to take measures to protect it from unauthorized actions, then at the end In the end, the sanction for access to information in the information system is still given by its operator (by prior agreement with the owner of the information). If there is no such contract, then by his actions to enter information into someone else's information system, the user actually provides access to it to the operator of the information system, which makes the latter its legal owner. From which, again, it follows that the operator will determine the mode of "technical access" to the information system.
Spy KGB Spy allows you to set an invisible mode of operation, so that no one will guess that it is monitored by a real keylogger. KGB Spy discreetly monitors the operation of the computer: records information entered from the keyboard, data from the clipboard, monitors visited sites.

How to detect and remove KGB Spy.
How to protect your personal information with Mask S.W.B from one of the most popular keyloggers - KGB Spy.
How can a computer user who does not have knowledge in the field of information security detect a spy hidden in his system and protect himself from surveillance without removing the keylogger from the computer in order to mislead the one who is following you? And how to remove the spy KGB Spy if you choose to do so? Consider the situation on the example of a common keylogger KGB spy and programs Mask S.W.B, which creates a secure platform for the user.
After launching Mask S.W.B anti-spyware, click the "System Processes" button.

In the system processes window, you can see all running processes, except for hidden ones.
To see if you have programs on your computer that hide themselves, click the Hidden Processes button.

Scroll to the bottom of the Hidden Processes window. All hiding programs (rootkits) will be highlighted in red.

In the picture above, we see a spyware called KGB spy. This keylogger is configured to hide its actions and spy on the user.
If you want to remove Kgb Spy, select "Open application folder" from the context menu.

In the window that opens, run the uninstallation of the program and the spyware will be removed.

If you just want to hide your actions from a keylogger and thereby mislead someone who is following you, then log into the platform by clicking the button with the name of the program, as shown in the figure above.
Inside the protection platform, those programs that hide themselves from the user (rootkits) can simply be seen in the process window.

Program Mask S.W.B creates a safe environment in which you can do everything, but the user's behavior becomes uncontrollable for spyware.

Spies will not be able to see your actions performed in a secure platform, which means that it will not be possible to transfer information about them to their owners either. Mask S.W.B protects against taking video from the monitor screen, from taking screenshots, does not allow receiving data from the keyboard and clipboard. In addition, it hides the sites you have visited and other information about your activities.
If you find a spy that your wife or your husband (well, or the boss at work) has set for you, do not rush to delete it. Think about it: it might be better for them to think that you are not doing anything unknown to them on the computer, since the spy will be clean. And in the meantime you can in the platform Mask S.W.B do what you wish.
In the picture below, we see that the KGB spy, after performing actions in the Mask S.W.B cloaking platform, could not fix anything.

The masking program hides the user's actions from all currently existing spies. With its help, you can detect and destroy computer spies that work at the level of kernel system drivers and are invisible to antivirus programs.
Download the anti-spyware program Mask S.W.B and check if you are being tracked with KGB spyHow to protect your personal information with COVERT from one of the most popular keyloggers - KGB Spy.
How can a computer user who does not have knowledge in the field of information security detect a spy hidden in his system and protect himself from surveillance without removing the keylogger from the computer in order to mislead the one who is following you? And how to remove Kgb Spy if you choose to do so? Let's consider the situation on the example of the widespread keylogger KGB spy and the COVERT program, which creates a secure platform for the user.
After launching the COVERT program, click the "System Processes" button.

In the system processes window, you can see all running processes, except for hidden ones.
To see if you have programs on your computer that hide themselves, click the Hidden Processes button.

Scroll to the bottom of the Hidden Processes window. All hiding programs (rootkits) will be highlighted in red.

In the picture above, we see a spyware called KGB spy. This keylogger is configured to hide its actions and spy on the user.
If you want to remove Kgb Spy, select "Open application folder" from the context menu.

In the window that opens, run the uninstallation of the program and the spyware will be removed.

If you just want to hide your actions from a keylogger and thereby mislead someone who is following you, then log into the platform by clicking the button with the name of the program, as shown in the figure above.
Inside the protection platform, those programs that hide themselves from the user (rootkits) can simply be seen in the process window.

The COVERT program creates a safe environment in which you can do everything, but the user's behavior becomes uncontrollable for spyware.


Spies will not be able to see your actions performed in a secure platform, which means that it will not be possible to transfer information about them to their owners either. COVERT protects against taking video from the monitor screen, from taking screenshots, and does not allow receiving data from the keyboard and clipboard. In addition, it hides the sites you have visited and other information about your activities.
If you find a spy that your wife or your husband (well, or the boss at work) has set for you, do not rush to delete it. Think about it: it might be better for them to think that you are not doing anything unknown to them on the computer, since the spy will be clean. In the meantime, you can do whatever you want in the COVERT platform.
In the picture below, we see that the KGB spy, after the actions performed in the COVERT cloaking platform, could not fix anything. The masking program hides the user's actions from all currently existing spies. With its help, you can detect and destroy computer spies that work at the level of kernel system drivers and are invisible to antivirus programs.

The functionality of the program allows you to set the invisible mode of operation, so that no one will guess that a real keylogger is following him. KGB Spy at computer work: records information entered from the keyboard, data from the clipboard, monitors visited sites.
The information collected during monitoring is stored in a database to which only you have access. You can receive a letter to your email box with detailed information about who, when and what did on the computer. You just need to check your mail from time to time.
If your computer is used not only by you, but also by your child, the problem becomes full-blown. There are enough resources on the Internet that are categorically not suitable for viewing by children.
In addition, cases of crimes committed against children by persons using Internet chats to seduce minors have recently become more frequent. It is extremely difficult to restrict a child's access to dubious resources, and it is almost impossible to prohibit access to chats. The best solution may be to use a monitoring system for your child's actions on the computer and on the Internet.
Sales of your company fell by 50% and the best manager began to behave inappropriately sometimes? When you enter, he frantically presses something on the keyboard! If you need to control the use of computing resources at the workplace by employees of your organization, you cannot do without a computer control and monitoring system.

There are both hardware solutions, such as, and hardware and software systems that combine the use of a simple video camera with the included software. Such solutions have both advantages and a number of disadvantages, starting with their high cost and ending with their incomplete compliance with the task of tracking the efficiency of operation, as well as the misuse of computer technology.
Provides a convenient, intuitive interface for tracking user activity on your computer. The product is able to track and save sequences of keystrokes to a file on your hard drive, allowing you to monitor the productivity of employees in the workplace or ensure the safety of your child in chats.
Or have you recently begun to think that your beloved is from you? Not a single message is stored in its ICQ, all files from the computer were transferred to a USB flash drive, it works on the Internet only when you are not around! All visited websites are also added to the report along with illustrations - instant screenshots!
You cannot understand what is happening. You are not offered for a child, loved one or employee - you are offered a reliable assistant in obtaining the necessary information - a spy program.
A unique feature of the product is a system for responding to the input of certain keywords or phrases.
Can send you an E-Mail or otherwise notify you if a user enters a keyword from the list you specify.





Tips&Tricks in Adobe illustrator: Tricks in illustrator
Windows won't boot after installing updates
Windows won't boot after installing updates
AVG Internet Security - free license
AVG Internet Security - free license