Lying is a whole technology that has the name "Social Engineering". High-quality lies are an integral part of "Social Engineering", without the use of which, in modern conditions, not a single cracker, both a beginner and a hardened one, can do.
Crackers are different: computer workstation hacker, server hacker, computer network hacker, telephone network hacker, cracker ( bearer) just the brain, etc. - and all of them use “Social Engineering” as an auxiliary tool, or just a lie, on which “Social Engineering” is basically built, and in fact most of the life of all mankind.
As children, we were taught not to lie. Nobody ever. However, as often happens, life crosses out all school lessons and stubbornly pokes us into the fact that without untruth, neither here nor there, - “You won’t lie, you won’t live.” The very best liars lie, surprisingly, sometimes and almost never admit it. We will talk about other secrets of the art of lying in this article.
Almost all spheres of human life, including religion, are permeated with lies, and restless British researchers of everything and everything in the whole wide world and adjacent galaxies also add: “It turns out that every person lies about 88 thousand times in his life! ".
The list of the most popular lies includes, of course, the well-worn ones: “There is no dough, now I’m broke myself”, “I’m very glad to see you”, “We will call you back” and “Thank you very much, I’m really very good. Like ". It turns out that everyone lies, to everyone and every time. But some people lie wonderfully, amusing others and making life easier for themselves, while others - not quite, while bringing pain and suffering to everyone around.
So, how can you learn to simply, safely and beautifully “powder your brains” ( hang noodles on your ears, drive a blizzard, deceive)? In this craft, as in any other, there are unwritten laws and secrets.
“The professor, of course, is a burdock, but the equipment is with him, with him. How is it heard? »

Big and small lies require the same scrupulous attitude
This is one of the basic rules that the upcoming master of lies must memorize. Each of your lies, regardless of its meaning, will have to be remembered forever and the subsequent lies will be built taking into account the previous one. However, it may seem to some that it is enough just to remember the most basic lie, and lies in petty formalities are not worth remembering. This is how, as a rule, inexperienced liars burn - having piled up a mountain of lies, they then forget who, when and how they “combed their hair”.
Therefore, strive to remember every one of your own, even the smallest, lies. And because the human memory is not infinite and you certainly won’t be able to remember all your “gonilovo”, then the main rule follows from this conclusion: Lie as rarely as possible, IMHO, this is the only way you can achieve credibility.
Sand in the eyes, noodles in the ears
A true master (driver) of lies is like a Spanish bullfighter who draws his sword only at the most decisive moment and inflicts only 1 blow. All the rest of the time, he masterfully distracts the victim with the help of deft manipulations of the red cloak. In the course of hanging noodles on the ears, similar methods are used, and deftly switching the interlocutor's attention to another object or changing the topic of the conversation from time to time generally relieves you of the need to lie. Think over your behavior strategy in advance so that you don’t have to drive any blizzard at all. Yes, look, do not overdo it, because the awkward use of the muleta can cost the bullfighter a lifetime!
Hard at school, easy at work
In any profession, practical training is necessary, and in such a profession as a liar, practice is definitely indispensable. But because it is not very humane to practice on living people, we will practice on ourselves. Let's stand in front of the mirror and repeat our lies until it starts to look completely natural. Ideally, we should convince ourselves of the veracity of our lies. The flawless deception is the one that we ourselves believed.
And I, then not me, and nonsense is not mine
If they began to suspect you of lying, then the worst thing that can be done in such a situation is to start making your own excuse and start inventing more and more lies. When the house began to stagger, then it is necessary to run away from it as soon as possible, and not urgently complete the construction of additional floors. That is why any accusations must be answered with insulted and proud silence, or else move out to a different topic.
Regarding "voluntary surrender to anal captivity", such surrender is tantamount to a direct shot in the temple. Often there are circumstances when the truth is equally flawed for both sides and the opposite side, despite its accusations of lying, like the liar himself, would not want to hear it. Do not back down and do not give up, even when you are literally pressed against the wall. Rot your line against evidence, logic and common sense ( there are no our troops in Crimea - this is all people's self-defense).
Only you, only me
You can think over the strategy of behavior for many moves ahead, you can work out brilliant acting skills near the mirror and work out the truthful intonations of the conversation, come up with an excuse, provide yourself with witnesses, escape routes and a second line of defense.
And relatives and friends can still find out the truth. It cannot be scientifically explained, because we do not believe in the type of “I dreamed in a dream” or “I feel my ass in my heart” ... “that you are a science fiction liar”. To put it another way, a kind of psycho-physiological non-verbal (astral) connection can be established between certain people, thanks to which they unconsciously feel the smallest modifications of each other's state. therefore, it is preferable not to even try to lie to relatives and friends.
In recent years, cybercriminals using social engineering techniques have adopted more advanced methods that make it more likely to gain access to the necessary information using the modern psychology of employees of enterprises, and people in general. The first step in countering these types of tricks is to understand the attackers' tactics themselves. Let's look at eight main approaches to social engineering.
Introduction
In the 90s, the concept of “social engineering” was introduced by Kevin Mitnick, an iconic figure in the field of information security, a former serious hacker. However, attackers used such methods long before the term itself appeared. Experts are convinced that the tactics of modern cybercriminals are tied to the pursuit of two goals: stealing passwords, installing malware.
Attackers are trying to apply social engineering using the phone, email and the Web. Let's get acquainted with the main methods that help criminals get the confidential information they need.
Tactic 1. The theory of ten handshakes
The main goal of an attacker using a phone for social engineering is to convince his victim of one of two things:
- The victim receives a call from a company employee;
- A representative of an authorized body calls (for example, a law enforcement officer or an auditor).
If a criminal sets himself the task of collecting data about a particular employee, he can first contact his colleagues, trying in every possible way to get the data he needs.
Do you remember the old theory of six handshakes? So, security experts say that there can be only ten “handshakes” between a cybercriminal and his victim. Experts believe that in modern conditions it is always necessary to have a little paranoia, since it is not known what this or that employee wants from you.
Attackers usually contact a secretary (or someone in a similar position) to gather information about people higher up in the hierarchy. Experts note that a friendly tone helps scammers a lot. Slowly but surely, criminals pick up the key to you, which soon leads to the fact that you share information that you would never have discovered before.
Tactic 2. Learn corporate language
As you know, each industry has its own specific formulations. The task of an attacker trying to obtain the necessary information is to learn the features of such a language in order to more skillfully use social engineering techniques.
All the specifics lie in the study of the corporate language, its terms and features. If a cybercriminal speaks a familiar, familiar and understandable language for his purposes, he will more easily gain confidence and be able to quickly get the information he needs.
Tactic 3: Borrow Music to Wait During Calls
To carry out a successful attack, fraudsters need three components: time, perseverance and patience. Often cyberattacks using social engineering are carried out slowly and methodically - not only data on the right people are collected, but also the so-called "social signals". This is done in order to gain trust and circle the target around your finger. For example, attackers can convince the person they are communicating with that they are colleagues.
One of the features of this approach is to record the music that the company uses during calls, at a time when the caller is waiting for an answer. The criminal first waits for such music, then records it, and then uses it to his advantage.
Thus, when there is a direct dialogue with the victim, the attackers at some point say: "Wait a minute, there is a call on the other line." The victim then hears familiar music and is left in no doubt that the caller represents a certain company. In essence, this is just a competent psychological trick.
Tactic 4. Spoofing (substitution) of a phone number
Criminals often use phone number spoofing to help them spoof the caller's number. For example, an attacker can sit in his apartment and call a person of interest, but the caller ID will display a company-owned number, which will create the illusion that the fraudster is calling using a corporate number.
Of course, unsuspecting employees will in most cases hand over sensitive information, including passwords, to the caller if the caller ID belongs to their company. This approach also helps criminals avoid tracking, as if you call this number back, you will be redirected to the company's internal line.
Tactic 5: Using the News Against You
Whatever the headlines of the current news, attackers use this information as bait for spam, phishing and other fraudulent activities. No wonder experts have recently noted an increase in the number of spam emails, the topics of which relate to presidential campaigns and economic crises.
Examples include a phishing attack on a bank. The email says something like this:
“Another bank [bank name] is acquiring your bank [bank name]. Click on this link to make sure your bank information is up to date before the deal is closed."
Naturally, this is an attempt to get information with which scammers can enter your account, steal your money, or sell your information to a third party.
Tactic 6: Leverage Trust in Social Platforms
It's no secret that Facebook, Myspace and LinkedIn are hugely popular social networks. According to expert research, people tend to trust such platforms. A recent spear-phishing incident targeting LinkedIn users supports this theory.
Thus, many users will trust an email if it claims to be from Facebook. A common trick is to claim that the social network is undergoing maintenance, you have to "click here" to update the information. That is why experts recommend that employees of enterprises enter web addresses manually to avoid phishing links.
It's also worth bearing in mind that sites will very rarely ask users to change their password or update their account.
Tactic 7. Typesquatting
This malicious technique is notable for the fact that attackers use the human factor, namely errors when entering a URL in the address bar. Thus, making a mistake of just one letter, the user can get to a site created specifically for this purpose by attackers.
Cybercriminals carefully prepare the ground for typesquatting, so their site will be like two peas in a pod similar to the legitimate one you originally wanted to visit. Thus, by making a mistake in writing a web address, you end up on a copy of a legitimate site, the purpose of which is either to sell something, or steal data, or distribute malware.
Tactic 8: Using FUD to Influence the Stock Market
FUD is a psychological manipulation tactic used in marketing and propaganda in general, which consists in presenting information about something (in particular, a product or organization) in such a way as to sow uncertainty and doubt in the audience about its qualities and thus cause fear of it.
According to the latest research from Avert, the security and vulnerability of products and even entire companies can affect the stock market. For example, researchers studied the impact of events such as "Microsoft Patch Tuesday" on the company's stock, finding a marked fluctuation each month after a vulnerability was released.
You can also recall how the attackers in 2008 spread false information about the health of Steve Jobs, which led to a sharp drop in Apple shares. This is the most typical example of FUD being used for malicious purposes.
In addition, it is worth noting the use of e-mail to implement the “pump-and-dump” technique (a scheme for manipulating the exchange rate in the stock market or in the cryptocurrency market with a subsequent collapse). In this case, the attackers can send out emails describing the amazing potential of the shares they bought up in advance.
Thus, many will try to buy these shares as soon as possible, and they will increase in price.
conclusions
Cybercriminals are often very creative in their use of social engineering. Having familiarized themselves with their methods, we can conclude that various psychological tricks are very helpful for attackers to achieve their goals. Based on this, it is worth paying attention to any little thing that can unwittingly give out a fraudster, check and double-check information about people contacting you, especially if confidential information is being discussed.
Don't lose. Subscribe and receive a link to the article in your email.
Since the advent of computers and the rise of the Internet, programmers have been working hard to ensure computer security. But even today, no one has been able to achieve this 100%. However, let's imagine that this result is still achieved thanks to the most powerful cryptography, enhanced security protocols, reliable software and other security elements. As a result, we get an absolutely secure network, and we can safely work in it.
"Wonderful! - you say, - it's in the bag! ”, But you will be wrong, because this is not enough. Why? Yes, because the benefit of any computer system can only be obtained with the participation of users, i.e. people. And it is precisely this interaction between a computer and a person that carries a serious danger, and a person is often the weakest link in the chain of security measures. Moreover, he himself is the reason why security is ineffective.
In the information age, it has become easier to manipulate people, because there is the Internet and mobile communications that allow you to interact without direct contact. There are even special methods that help attackers "operate" on people the way they want. Their complex is called social engineering, and in this article we will try to find out what it is.
Social engineering: what is it and how did it appear?
It is easy to guess that even the most sophisticated security system is vulnerable when it is controlled by a person, especially if this person is gullible, naive and. And when an attack is made on a machine (PC), not only the computer, but also the person who works behind it, can act as a victim.
It is this attack in the slang of social hackers called social engineering. In its traditional form, it looks like a phone call, where the caller pretends to be someone else, wanting to extract confidential information from the subscriber, most often passwords. But in our article we will consider the phenomenon of social engineering in a broader sense, meaning by it any possible methods of psychological manipulation, such as blackmail, playing on feelings, deceit, etc.
In this understanding, social engineering is a method of controlling people's actions without the use of technical means. Most often, it is perceived as an illegal method of obtaining various valuable information. It is mainly used on the Internet. If you are interested in examples of social engineering, then here is one of the most striking:
EXAMPLE: An attacker wants to learn the password from a person's personal Internet banking account. He calls the victim on the phone and introduces himself as a bank employee, asking for a password, referring to serious technical problems in the organization's system. For greater persuasiveness, he names the fictitious (or real) name of the employee, his position and powers (if necessary). To make the victim believe, the social hacker can fill his story with believable details, play on the feelings of the victim himself. After the attacker has received the information, he still skillfully says goodbye to his “client”, and then uses the password to enter his personal account and steal funds.
Oddly enough, but even in our time there are people who peck at such bait, and trustingly tell social hackers everything they need. And in the arsenal of the latter there can be many techniques and techniques. We will also talk about them, but a little later.
Social engineering is a science (direction) that has appeared relatively recently. Its sociological significance lies in the fact that it operates with specific knowledge that guides, systematizes and optimizes the process of creating, modernizing and applying new social realities. In a sense, it complements sociological knowledge, transforming scientific knowledge into algorithms of activity and behavior.
Humans have been using social engineering in some form since ancient times. For example, in ancient Rome and ancient Greece, specially trained rhetoricians were highly respected, able to convince the interlocutor of his “wrongness”. These people participated in diplomatic negotiations and solved state problems. Later, social engineering was adopted by intelligence agencies such as the CIA and the KGB, whose agents successfully impersonated anyone and found out state secrets.
By the early 1970s, telephone hooligans began to appear, breaking the peace of various companies for the sake of a joke. But over time, someone realized that if you use a technical approach, you can easily get various important information. And by the end of the 70s, the former telephone hooligans turned into professional social engineers (they began to be called singers), capable of skillfully manipulating people, defining their complexes and fears by mere intonation.
When computers appeared, most singers changed their profile, becoming social hackers. Now the concepts of "social engineering" and "social hackers" are synonymous. And with the powerful development of social engineering, new types of it began to appear and the arsenal of techniques expanded.
Watch this short video to find out how social hackers manipulate people.
Social engineering methods
All real examples of social engineering show that it easily adapts to any conditions and to any environment, and the victims of social hackers, as a rule, do not even suspect that some kind of technique is being used against them, and even more so they do not know who does it.
All social engineering methods are based on . This is the so-called cognitive basis, according to which people in a social environment always tend to trust someone. Among the main methods of social engineering are:
- "Trojan horse"
- Pretexting
- "Road Apple"
- Phishing
- Qui pro quo
Let's talk about them in more detail.
"Trojan horse"
When using a "Trojan horse", a person's curiosity and his desire to benefit are exploited. Social hackers send a letter to the victim's E-Mail containing some interesting attachment, for example, an upgrade for some program, a screen saver of erotic content, exciting news, etc. The method is used to force the user to click on a file that can infect the computer with a virus. Often, as a result, banners appear on the screen, which can be closed in only two ways: by reinstalling the operating system or by paying the attackers a certain amount.
Pretexting
The term "pretexting" means an action that the user performs according to a previously prepared pretext, i.e. scenario. The goal is for a person to give out specific information or perform a specific action. In most cases, pretexting is used for phone calls, although there are examples of such attacks on Skype, Viber, ICQ and other instant messengers. But to implement the method, a singer or a hacker must not only, but also conduct a study of the object in advance - find out his name, date of birth, place of work, amount on the account, etc. With the help of such details, the singer increases the victim's confidence in himself.
"Road Apple"
The road apple method consists in adapting a "Trojan horse" and requires the mandatory use of some kind of physical storage medium. Social hackers can plant bootable flash drives or discs tampered with media with interesting and/or unique content. All that is needed is to discreetly place a “travel apple” on the victim, for example, in a car in a parking lot, in a bag in an elevator, etc. Or you can just leave this "fruit" where the victim will most likely see it and take it herself.

Phishing
Phishing is a very common method of obtaining sensitive information. In the classic version, this is an “official” e-mail (from a payment service, a bank, a high-ranking individual, etc.), equipped with signatures and seals. The recipient is required to follow a link to a fake site (there is also everything that says about the "officiality and reliability" of the resource) and enter some information, for example, full name, home address, phone number, addresses of profiles in social networks, bank number cards (and even a CVV code!). Having trusted the site and entered the data, the victim sends them to the scammers, and what happens next is easy to guess.
Qui pro quo
The Qui Pro Quo method is used to introduce malware into the systems of various companies. Social hackers call the right (sometimes any) company, introduce themselves as technical support employees and interrogate employees for any technical malfunctions in the computer system. If there are malfunctions, the attackers begin to "fix" them: they ask the victim to enter a certain command, after which it becomes possible to launch virus software.
The above methods of social engineering are most common in practice, but there are others. In addition, there is also a special type of social engineering, which is also designed to influence a person and his actions, but is done according to a completely different algorithm.
Reverse social engineering
Reverse social engineering and the social hackers who specialize in it build their activities in three directions:
- Situations are created that force people to seek help
- Problem-solving services are advertised (this includes being ahead of the help by real experts)
- It turns out "help" and impact
In the case of this type of social engineering, attackers initially study the person or group of people they plan to influence. Their passions, interests, desires and needs are investigated, and the influence is exerted through them with the help of programs and any other methods of electronic influence. Moreover, the programs must first work without failures so as not to cause concern, and only then switch to a malicious mode.
Examples of reverse social engineering are also not uncommon, and here is one of them:
Social hackers develop a program for a specific company, based on its interests. The program contains a slow-acting virus - after three weeks it is activated, and the system begins to malfunction. The management is contacting the developers to help fix the problem. Being ready for such a development of events, the attackers send their "specialist", who, "solving the problem", gains access to confidential information. The goal has been reached.
Unlike conventional social engineering, reverse is more time-consuming, requires special knowledge and skills, and is used to influence a wider audience. But the effect of it is amazing - a victim without resistance, i.е. at his own request, he reveals all the cards to the hackers.
Thus, any kind of social engineering is almost always used with malicious intent. Some people, of course, talk about its benefits, pointing out that it can be used to solve social problems, maintain social activity, and even adapt social institutions to changing conditions. But, despite this, it is most successfully used for:
- Deceive people and obtain confidential information
- Manipulating and blackmailing people
- Destabilization of the work of companies for their subsequent destruction
- Database theft
- Financial fraud
- Competitive Intelligence
Naturally, this could not go unnoticed, and methods of counteracting social engineering appeared.
Protection against social engineering
Today, large companies systematically conduct all kinds of tests for resistance to social engineering. Almost never the actions of people who have fallen under the attack of social hackers are not intentional. But that's why they are dangerous, because if it is relatively easy to defend against an external threat, then it is much more difficult to defend against an internal one.
To improve security, company management conducts specialized trainings, controls the level of knowledge of its employees, and also initiates internal sabotage itself, which allows you to determine the degree of preparedness of people for attacks by social hackers, their reaction, conscientiousness and honesty. So, “infected” letters can be sent to E-Mail, make contact on Skype or social networks.
The very same protection against social engineering can be both anthropogenic and technical. In the first case, people's attention is drawn to security issues, the essence of the seriousness of this problem is conveyed and measures are taken to instill a security policy, methods and actions are studied and implemented that increase the protection of information support. But all this has one drawback - all these methods are passive, and many people simply ignore the warnings.
As for technical protection, this includes means that impede access to information and its use. Considering that emails and messages have become the most “popular” attacks of social hackers on the Internet, programmers create special software that filters all incoming data, and this applies to both private mailboxes and internal mail. Filters analyze the texts of incoming and outgoing messages. But there is a difficulty here - such software loads servers, which can slow down and knock down the system. In addition, it is impossible to foresee all variations of writing potentially dangerous messages. However, technology is improving.
And if we talk specifically about the means that prevent the use of the data obtained, they are divided into:
- Blocking the use of information everywhere except the user's workplace (authentication data is tied to electronic signatures and serial numbers of PC components, physical and IP addresses)
- Blocking the automatic use of information (this includes the familiar Captcha, where the password is a picture or its distorted part)
Both of these methods block the possibility of automation and shift the balance between the value of information and the work of obtaining it towards work. Therefore, even with all the data given out by unsuspecting users, social hackers face serious difficulties in their practical application.
And for any ordinary person, to protect against social engineering, we advise you to simply remain vigilant. When receiving an e-mail letter, be sure to carefully read the text and links, try to understand what is in the letter, from whom it came and why. Don't forget to use antiviruses. If unknown people call from an unknown number, never give out your personal data, especially those related to your finances.
By the way, this video, albeit briefly, but interestingly, talks about how to protect yourself from social engineering.
And, finally, we want to introduce you to some of the books on social engineering, including as a field of sociological knowledge, so that if you wish, you can get to know the topic in more detail.
These books are full of practical advice on how to master common manipulative techniques and tricks. You will also learn about the most effective methods of social engineering and learn how to recognize them and defend against attacks.
Books on social engineering:
- Kevin Mitnick "Ghost on the Web"
- Kevin Mitnick, William Simon "The Art of Invasion"
- Kevin Mitnick, William Simon "The Art of Deception"
- Chris Kaspersky "The Secret Weapon of Social Engineering"
Remember that everyone is capable of mastering the art of controlling the actions of others, but these skills must be used for the benefit of people. Sometimes it is useful and convenient to guide a person and push him to decisions that are beneficial to us. But it is much more important to be able to identify social hackers and cheaters so as not to become their victim; it is much more important not to be one of them yourself. We wish you wisdom and useful life experience!
Usually, social engineering is a set of techniques aimed at making a person behave in a certain way, as someone needs, for example, to give money, provide secret information, or sign something. In order to do this, it is usually necessary to study the human factor, people's reactions to requests, complaints, sources of stress, and so on. Knowing the attitudes and reactions of most people, it is easy to get certain actions from them.
How social engineering is related to fraud and how it is used to extract forbidden information.
Consider social engineering from these two points of view. You may have noticed that scammers are always particularly active during economic times. In this age of technology, they are becoming more prepared and trained. At their service are psychology, social engineering, IT technologies and many other special knowledge that help manage people's actions. Of course, there will not be enough time to study all their tricks, but it is still useful to pay attention to the basic principles of tricks and technologies that they use in order not to fall into the set networks.
What kind of people are most likely to become? How to be a victim of people and circumstances? ? How about us? About this and not only, we have already written on our website. Now briefly about a special science - the knowledge from which is used by "advanced" scammers - social engineers.
Social engineering as a science.
Social engineering is a fairly young science that includes knowledge of the psychology of people and their behavior in critical situations. Social engineering can also be called "a piggy bank of human errors", since this science absorbs everything related to the human factor and its use.
Such knowledge makes it possible to predict possible variants of a person's behavior and design various situations in order to bring him to a certain reaction. Provoked by a fraudster - a social engineer - the reaction leads a person to those actions that were originally the goal of the fraudster. What could be its purpose? Of course, to ferret out information or infiltrate someone else's territory or just get your money. In this regard, social engineers are also called social hackers.
What kind of person is this social engineer?
This person possesses and skillfully uses knowledge from social engineering. This is a "psychologist" (not a professional, of course), who takes into account complexes, weaknesses, prejudices, habits, reflexes, etc. people.
Kevin Mitnick, who used to be a social hacker and now a security consultant, said that it's much easier to lure out the right information with tricks than to come up with various hacking programs.
How to protect yourself from "social hackers"?
It can be very difficult, almost impossible, if you do not know anything about them. And, even knowing their tricks, you can fall for the bait, because they are experts in your spontaneous reactions, reflexes, automatisms, and so on. Be careful!
So, quite recently, in January of this year, the Internet was literally full of such news:
The calculation of the hackers was simple - the recipients of the mailing list will fulfill the request of the scammers on behalf of the management in order to avoid a reprimand from this management. And so it happened. According to the instructions of social hackers, bank employees of the Belgian bank Crelan performed the actions necessary for fraudsters without additional checks. The message from the hackers to the e-mail contained a request for an urgent completion of the transaction. It looked quite plausible, as the criminals used copies of company logos and well-known domains.
Psychologists conducted similar experiments before the situation with the Belgian bank. So researchers from England sent messages to employees of a large corporation on behalf of the system administrator of their company. The message contained a request to send passwords in connection with a scheduled check of the equipment. The result was sad - most of the employees (75%) followed the instructions of the attackers.
As you can see, human actions are quite easy to program. Moreover, quite smart, educated and highly intelligent people can fall for the bait of scammers. There is nothing strange here, given that there are other people who study the actions, automatisms, reactions of all kinds of different people. Including very smart ones.
EXAMPLES of using social engineering methods
One social engineer describes how he made his way into a restricted area using people's mindsets. Security guards are people too! This person (social engineer) observed what kind of badges the employees of the company he needed, made the same for himself, printed it out on a computer and went through the back door with the employees of the institution.
Of course, he did not have a door chip, but he used the "train" method. Its essence is simple. When a bunch of people accumulate in front of the door, it does not close completely and those who go in front hold the door for those who follow him. Usual courtesy. After all, they can see by the badge that this is also an employee. The guards see a bunch of people with identical badges and don't pay much attention to them. Moreover, not even an announcement hangs in large letters on the wall, but a poster warning that everyone should go through one at a time. You can not hold the door to the one walking behind for the sake of general safety! But, unless the company of acquaintances will do it? Who from this company will say to one of the people: "And you, please, go out and go back in with your key (chip), because I don't know you." The probability of this is very small. But that's exactly what you need to do.
So it turns out that employees violate security requirements with enviable constancy, and swindlers, with the same constancy, use the above-described automatisms. There will always be people who follow the lead of swindlers, no matter how much they are warned and taught. Social engineers are well aware of this and therefore do not bother much about what trick to come up with. They just use the same methods. After all, automatisms in people do not change much, that's why they are automatisms. Be original. Don't stereotype! Always be wary of unexpected or scary messages. Pay attention to warning notices.
The most used social engineering techniques are based on human weaknesses such as pity, fear, and the desire to get rich quick. If we talk about pity, then hackers use this trait of people in a variety of ways. For example, they send messages by phone or through social networks asking for help on behalf of your friends or relatives.
Basic methods and techniques of social engineering / social engineering
All methods of social engineering are based on the human factor, that is, on the peculiarities of the psyche of people: to panic, to react in the same way in certain circumstances, to lose vigilance, to get tired, to sympathize, to experience fear, and much more. For example, here are just some of the techniques, and you try to independently determine which feature of the psyche the social engineer used here:
- One of the plots can be like this: a friend is out of town, he can’t call himself right now - a serious problem, money is urgently needed. Asks to send to the account or bank card number. Let not everyone react positively, but only a certain percentage of respondents, the hacker knows that this will be the case. He does not care, because the messages programmed by him are sent by the machine. There are those who urgently help, without checking where these SMS come from. After all, a friend is in trouble .. And due to the urgency, many do not check the source.
- With the same calculation, some time ago, many women were sent SMS from their son, who was in trouble. Of course, he himself cannot call back until his mother sends money to solve this problem. And mothers sent, it is not known where and to whom. Without rechecking anything (so the son asked).
- Also, on behalf of friends they lure out personal information, send out malicious links with comments. For example: “Hi, do you want to laugh? Follow this link and you can listen to any telephone conversation (or SMS correspondence) that interests you. Or something like that, the main thing is that you click on the link.
There is also an option in the arsenal of social engineers when they "work" for the buyer. Many users put their things up for sale, for example on Avito. Such a “buyer” is looking for something more expensive (cars, houses, etc.), contacts a real seller and declares his desire to buy your not cheap thing. Of course, the seller is happy. Wow, how quickly, I did not have time to put up how everything was sold. He's already counting his income in his mind. True, the buyer regretfully reports that he will be able to call for the thing only after two or three days. Well, so that you don’t sell this valuable thing to someone else, he asks you to remove the ad from Avito and is ready to pay half or even 75% of the cost right today for a guarantee. “Of course!” You think, “With pleasure! Let him pay! The “buyer” asks to which card, he could transfer money to you. And you tell this stranger all the card details. Only instead of acquiring his money, you lose all your savings. He may also ask you to tell him the code that will come to your phone.
If we talk about such a trait as the desire to get rich quickly and without much effort, then this is such a vice, using which social engineers can invent and invent for a very long time. After all, people themselves are looking for these "adventures" and, even, are ready to step on the same rake. Therefore, scammers continue to portray: either a well-known brand that gives crazy gifts; then a company promising attractive discounts; then a bank offering to take a loan with a meager percentage; then an employer who will help you make easy money on the Internet or elsewhere ... Only, in order to get any of this, you must first provide card details ... After all, a newly-minted employer or a good bank must transfer money to you somewhere ... They reported card details to a stranger, you can say goodbye to its contents.
Why do you need to know about it?
Recently, interest in social engineering has become very high. This can be seen from the popularity of this request on the Internet. This means that the number of hackers and the demand for programs to protect against their attacks will only grow. And not only hackers, scammers of any kind use social engineering methods for their own purposes.
To be informed, then armed, you can read the literature on this topic:
Social engineering and social hackers. Maxim Kuznetsov, Igor Simdyanov.
Be careful! Don't let yourself be fooled.
Social engineering uses knowledge of psychology and the human factor. Be extremely careful, social hackers know you very well.
It would also be interesting to know if you knew about social engineering and the cunning tricks used by those people who are behind it?
Sincerely, site If you want to receive new articles, subscribe to our newsletter.
In this article, we will focus on the concept of "social engineering". Here the general will be considered. We will also learn about who was the founder of this concept. Let's talk separately about the main methods of social engineering that are used by attackers.
Introduction
Methods that allow you to correct human behavior and manage his activities without the use of a technical set of tools form the general concept of social engineering. All methods are based on the assertion that the human factor is the most destructive weakness of any system. Often this concept is considered at the level of illegal activity, through which the criminal performs an action aimed at obtaining information from the subject-victim in a dishonest way. For example, it could be some kind of manipulation. However, social engineering is also used by humans in legitimate activities. Today, it is most often used to access resources with sensitive or sensitive information.
Founder
The founder of social engineering is Kevin Mitnick. However, the concept itself came to us from sociology. It denotes a general set of approaches used by applied social. sciences focused on changing the organizational structure that can determine human behavior and exercise control over it. Kevin Mitnick can be considered the founder of this science, since it was he who popularized the social. engineering in the first decade of the 21st century. Kevin himself was previously a hacker who committed to a wide variety of databases. He argued that the human factor is the most vulnerable point of a system of any level of complexity and organization.

If we talk about social engineering methods as a way to obtain rights (often illegal) to use confidential data, then we can say that they have been known for a very long time. However, it was K. Mitnick who was able to convey the full importance of their meaning and the peculiarities of their application.
Phishing and non-existent links
Any technique of social engineering is based on the presence of cognitive distortions. Behavioral errors become a "tool" in the hands of a skilled engineer, who in the future can create an attack aimed at obtaining important data. Among the methods of social engineering, phishing and non-existent links are distinguished.
Phishing is an online scam designed to obtain personal information such as username and password.
Non-existent link - the use of a link that will lure the recipient with certain benefits that can be obtained by clicking on it and visiting a specific site. Most often, the names of large companies are used, making subtle adjustments to their name. The victim, by clicking on the link, will "voluntarily" transfer their personal data to the attacker.
Methods using brands, defective antiviruses and a fake lottery
Social engineering also uses brand name scams, defective antiviruses, and fake lotteries.
"Fraud and brands" is a method of deception, which also belongs to the phishing section. This includes emails and websites that contain the name of a large and/or "hyped" company. Messages are sent from their pages with notification of victory in a certain competition. Next, you need to enter important account information and steal it. Also, this form of fraud can be carried out over the phone.
Fake lottery - a method in which a message is sent to the victim with the text that he (a) won (a) the lottery. Most often, the alert is masked using the names of large corporations.
False antiviruses are software scams. It uses programs that look like antiviruses. However, in reality, they lead to the generation of false notifications about a particular threat. They also try to lure users into the realm of transactions.
Vishing, phreaking and pretexting
Speaking of social engineering for beginners, we should also mention vishing, phreaking and pretexting.

Vishing is a form of deception that uses telephone networks. It uses pre-recorded voice messages, the purpose of which is to recreate the "official call" of the banking structure or any other IVR system. Most often, they are asked to enter a username and / or password in order to confirm any information. In other words, the system requires authentication by the user using PINs or passwords.
Phreaking is another form of phone scam. It is a hacking system using sound manipulation and tone dialing.
Pretexting is an attack using a preconceived plan, the essence of which is to represent another subject. An extremely difficult way to cheat, as it requires careful preparation.
Quid Pro Quo and the Road Apple Method
The theory of social engineering is a multifaceted database that includes both methods of deception and manipulation, as well as ways to deal with them. The main task of intruders, as a rule, is to fish out valuable information.
Other types of scams include: quid pro quo, the road apple method, shoulder surfing, open source use, and reverse social media. engineering.

Quid-pro-quo (from lat. - “for this”) - an attempt to fish out information from a company or firm. This happens by contacting her by phone or by sending messages by e-mail. Most often, attackers pose as employees of those. support, which report the presence of a specific problem in the workplace of the employee. They then suggest ways to fix it, for example by installing software. The software turns out to be defective and promotes the crime.
"Road apple" is an attack method that is based on the idea of a Trojan horse. Its essence lies in the use of a physical medium and the substitution of information. For example, they can provide a memory card with a certain "good" that will attract the attention of the victim, cause a desire to open and use the file or follow the links indicated in the documents of the flash drive. The "road apple" object is dropped in social places and waited until the attacker's plan is implemented by some subject.
Gathering and searching for information from open sources is a scam in which data acquisition is based on the methods of psychology, the ability to notice little things and the analysis of available data, for example, pages from a social network. This is a fairly new way of social engineering.

Shoulder surfing and reverse social. engineering
The concept of "shoulder surfing" defines itself as the observation of the subject live in the literal sense. With this type of data fishing, the attacker goes to public places, such as a cafe, airport, train station and follows people.
Do not underestimate this method, as many surveys and studies show that an attentive person can receive a lot of confidential information simply by being observant.
Social engineering (as a level of sociological knowledge) is a means for "capturing" data. There are ways to obtain data in which the victim herself will offer the attacker the necessary information. However, it can also serve the benefit of society.
Reverse social engineering is another method of this science. The use of this term becomes appropriate in the case that we mentioned above: the victim himself will offer the attacker the necessary information. This statement should not be taken as absurd. The fact is that subjects endowed with authority in certain areas of activity often get access to identification data at the subject's own decision. Trust is the basis here.

Important to remember! Support staff will never ask the user for a password, for example.
Information and protection
Social engineering training can be carried out by an individual both on the basis of personal initiative and on the basis of benefits that are used in special training programs.
Criminals can use a variety of types of deception, ranging from manipulation to laziness, gullibility, courtesy of the user, etc. It is extremely difficult to protect yourself from this type of attack, due to the victim's lack of awareness that he (she) was deceived. Various firms and companies to protect their data at this level of danger are often engaged in the evaluation of general information. Next, the necessary protection measures are integrated into the security policy.
Examples
An example of social engineering (its act) in the field of global phishing mailings is an event that occurred in 2003. Emails were sent to eBay users during this scam. They claimed that the accounts belonging to them were blocked. To cancel the blocking, it was necessary to re-enter the account data. However, the letters were fake. They translated to a page identical to the official one, but fake. According to expert estimates, the loss was not too significant (less than a million dollars).

Definition of responsibility
The use of social engineering may be punishable in some cases. In a number of countries, such as the United States, pretexting (deception by impersonating another person) is equated with an invasion of privacy. However, this may be punishable by law if the information obtained during pretexting was confidential from the point of view of the subject or organization. Recording a telephone conversation (as a social engineering method) is also required by law and requires a fine of $250,000 or imprisonment for up to ten years for individuals. persons. Legal entities are required to pay $500,000; the period remains the same.


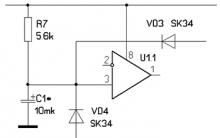
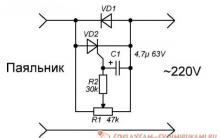

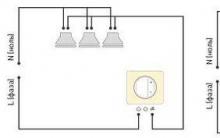





Battery not charging
The best navigation programs: rating of solutions for GPS navigators
How to set the date and time on your computer in two easy ways
Enable the Windows Installer service in safe mode How to enable uninstall programs in safe mode
Default archiver. Create ZIP archives. How winrar works